Upload cyber threat intelligence
Intelligence reports, blog posts, etc. are all supported. The more intelligence that goes in, the better the rules that are produced.
Deploy to Your Security Stack
SPL, KQL, YARA2, Elastic... our specially trained AI model can write detection rules for almost all SIEMs. Sync your rulesets automatically with these products for seamless hunting and detection.
Fully Managed Rules
As new intelligence, including alerts, are discovered, your ruleset is automatically tuned to improve detections.
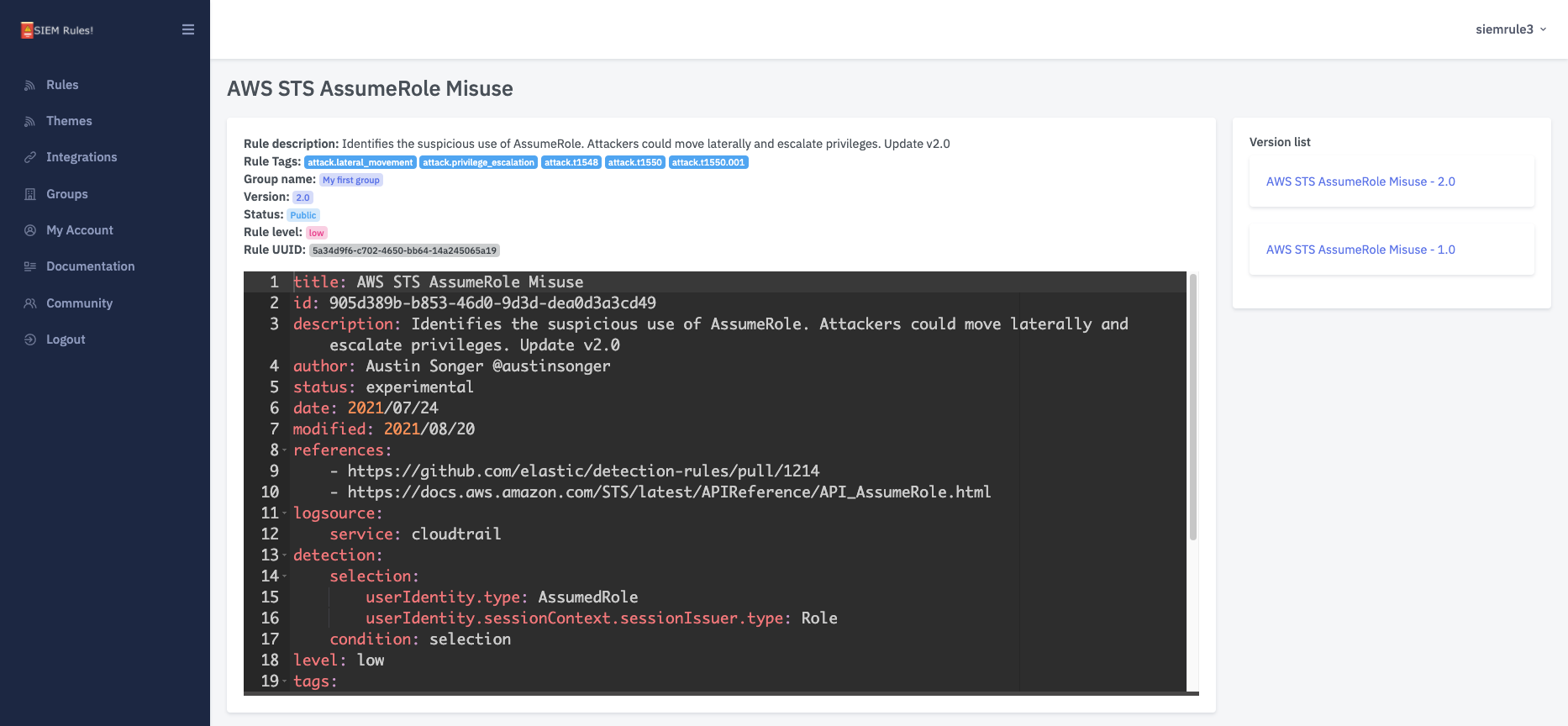
Discover New Rules
By selecting TLP:CLEAR or TLP:GREEN for your reports will share them with other SIEM Rules users. You'll also have full access to rules made public by other users.
Integrate Easily
SIEM Rules has been designed to to be supercharge other security tooling. Use our existing product integrations, or build your own using the SIEM Rules REST API and TAXII API.
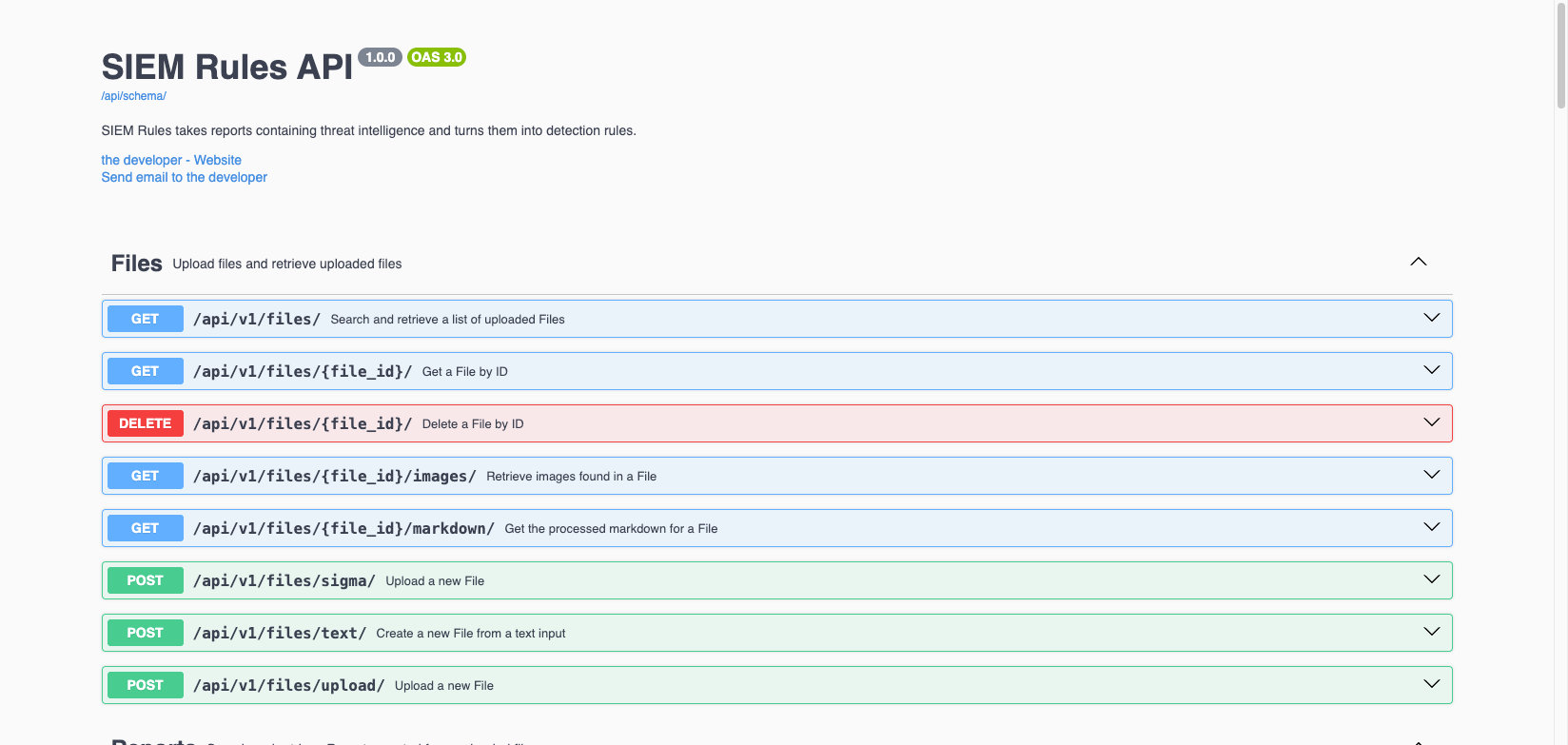
See How it Works
The core SIEM Rules API is available on GitHub under an Apache 2.0 license. Run the code yourself and contribute to future improvements of SIEM Rules.