Blog
The SIEM Rules blog
-
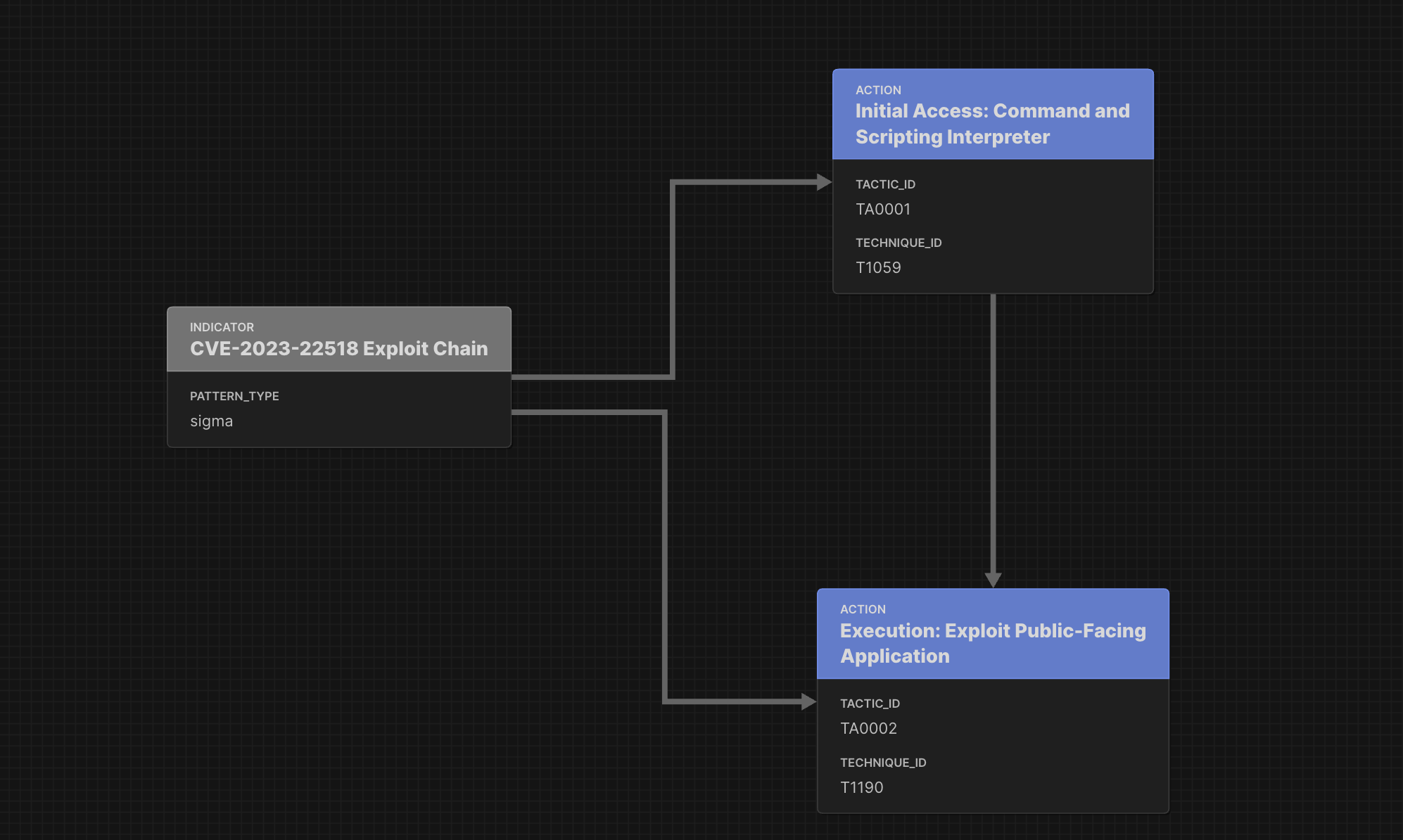
Using Sigma Rules inside Attack Flows as a Structured Way to Describe an Incident
TUTORIAL April 07, 2025
Many attacks are described using free text. This happens, then this, then this. Whereas detection rules provide a structured way to represent these descriptions with actionable content. Attack Flows are the perfect vehicle to combine the two approaches. -
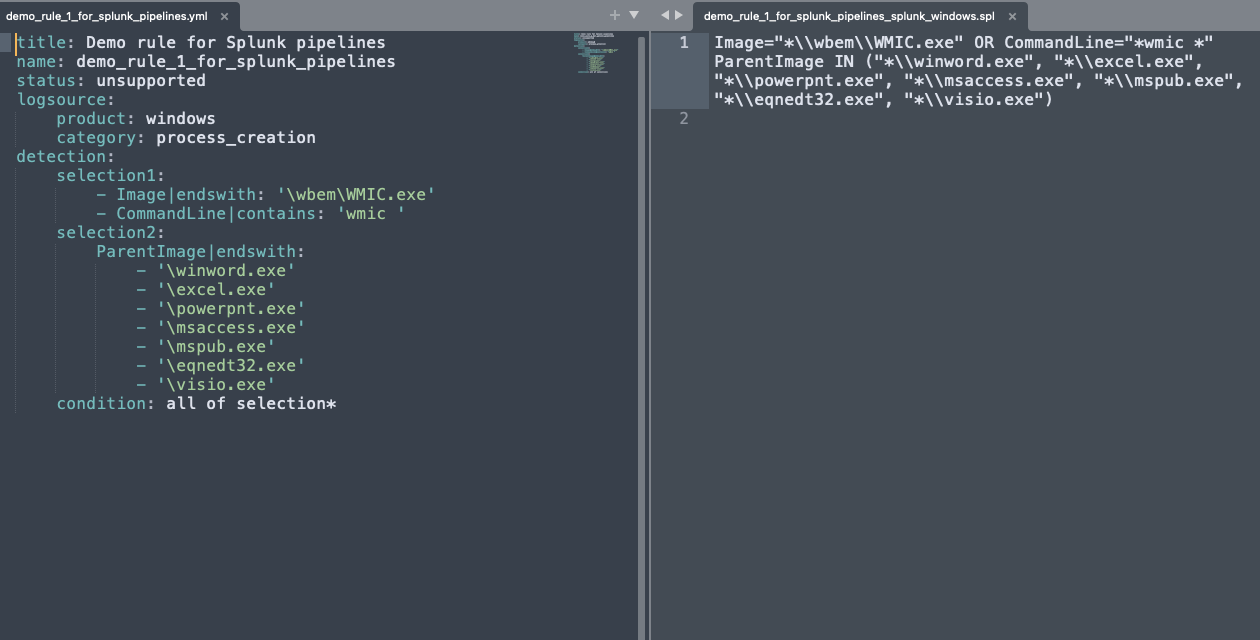
An Introduction pySigma: Converting Sigma Rules to Work with Your SIEM
TUTORIAL February 17, 2025
Learn how to seamlessly convert Sigma Rules into queries for your SIEM. Follow along with real examples. -
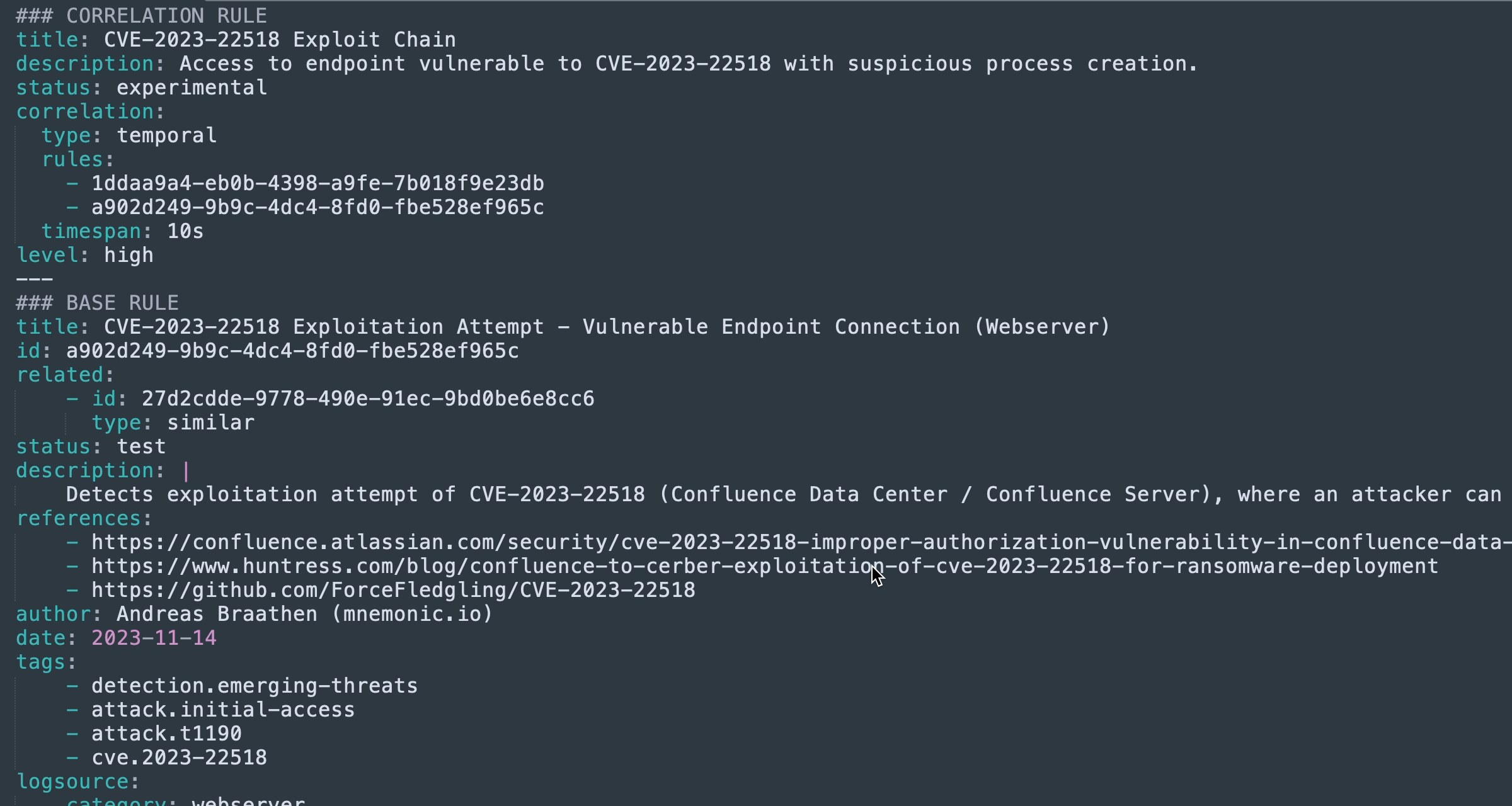
Writing Advanced Sigma Detection Rules: Using Correlation Rules
TUTORIAL January 27, 2025
Correlation Rules allow you to detect threats by linking multiple events together based on a meaningful relationship. -
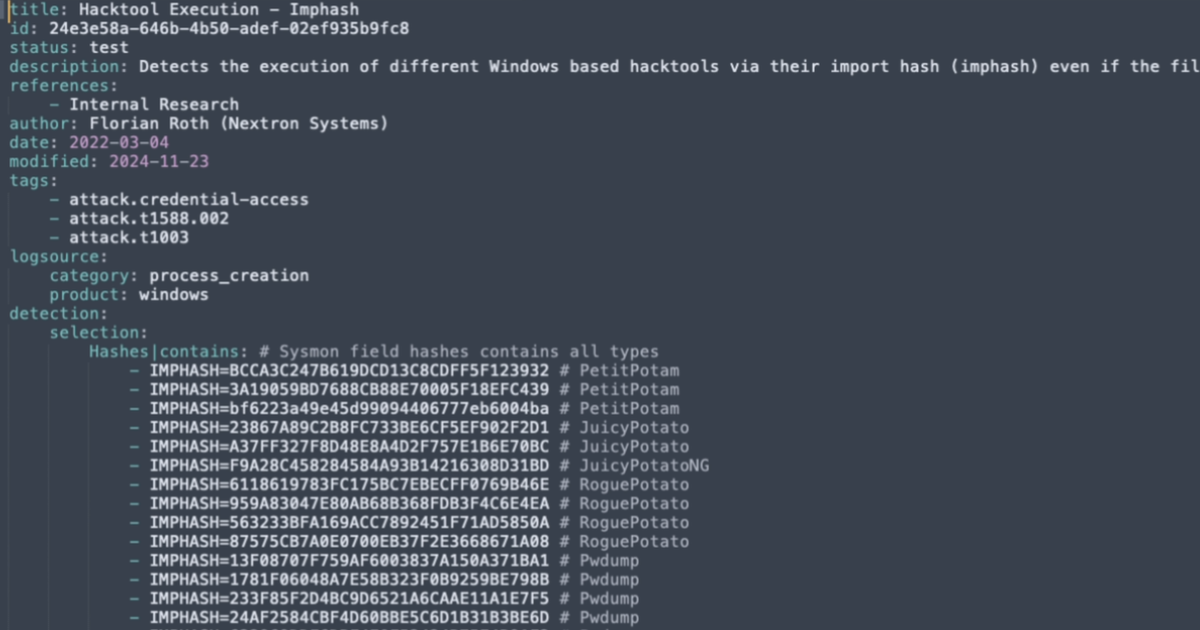
Writing Effective Sigma Detection Rules: A Guide for Novice Detection Engineers
TUTORIAL September 23, 2024
Sigma Rules are becoming more widely adopted as the standard detection language. Learning how to write them is not difficult. Let me show you.
